Phishing (pronounced like “fishing”) is a sneaky trick used by cyber-criminals to steal your personal information. They do this by pretending to be someone trustworthy, like a friend or a company you know.
These cyber-criminals send fake emails, create fake websites, or even send text messages (SMS) to trick you. Imagine they’re like digital fishing hooks trying to catch your sensitive information, such as credit card numbers, usernames, passwords, or Social Security numbers.
Here’s what you need to remember:
- Always be cautious when you receive messages, especially if they ask you to click on links or open attachments.
- Trust your instincts. If something feels off, it probably is!
- If you receive a suspicious message, delete it right away. Don’t click on any links or reply to it.
- To learn more about protecting yourself from phishing, watch a short video on the Microsoft Support Article titled “Protect yourself from phishing.” It explains how to spot these tricky messages.
- If you’re unsure whether a message is a phishing scam, check our current Phishing Examples and SMS Phishing (Smishing) Examples page. We post messages that others have reported.
- And if you don’t find your message there, report it to our email security team.
Asking you to Purchase or Give out Personal Information
If you receive a text from a coworker or classmate who has never messaged you outside of work or class, or if the message comes from an unfamiliar phone number, be cautious. It could be an SMS phishing attempt.
Here’s what to watch out for:
- Purchase Requests: If the text asks you to buy something for them, especially gift cards, treat it as suspicious.
- Personal Information: Be wary if they request your personal details, like credit card numbers or Social Security information.
What to Do:
- Don’t Respond: Avoid replying to such messages.
- Verify Legitimacy: If in doubt, reach out to the person using a trusted contact method (like their university email or official phone number) to confirm the request.
- Block Unknown Numbers: Consider blocking any unfamiliar numbers that send you suspicious links or ask probing questions.
How to Spot Deception Online
One of the best ways to protect yourself from scams is to be cautious about internet addresses and email domains. Here’s how:
Check the Domain Extension:
- Websites and email addresses often end with specific extensions like .com, .gov, or .edu.
- Ask yourself if the extension matches the purpose of the site. For example, a government site should end in .gov
- Be suspicious if a site or email uses a .com domain for something that should be official.
Watch for Country Codes:
- Sometimes a site’s name ends with a country code (e.g., .uk, .ro, .ru, or .ca).
- Consider whether it makes sense in context. Would your local bank email you from Romania? Probably not.
Red Flags:
- Concealed Web Addresses: Links may say one thing but lead somewhere different.
- Deceptive Addresses: Scammers create fake web addresses that look real.
- Forged Email Addresses: The “From” address in emails can be easily faked.
SMS Phishing:
- Be cautious of text messages that appear to come from email addresses with phone numbers.
- Look out for domains associated with wireless/text message companies (e.g., icloud.com, vtext.com, myvzw.com, momail.net, email.uscc.net). Example: +11234567890@myvzw.com
Watch Out for Deceptive Links
Scammers love using tricky links in emails and on web pages (especially ads). Here’s how it works:
The Mimic Trick:
- They create a link that looks like a legit web address.
- But when you click it, surprise! It takes you somewhere else entirely.
Example:
-
- Imagine you get an email from your university (let’s say UI).
- The link says: www.its.uiowa.edu/webmail. Sounds real, right?
- But behind the scenes, it’s more like: www.abc-bad-link.com/use/upgrade/form.html.
What Could Go Wrong?:
- Clicking a bad link can infect your computer with nasty stuff (malware).
- Infected systems can do anything—from stealing your info to spamming your friends.
How to Spot Deception:
- Hover First: Before clicking, hover your mouse over the link. The real destination should pop up (and might even warn you of a mismatch).
- Check URLs: Look closely - do they match what you expect?
- Be Wary of “Click Here”: Avoid links that don’t clearly say where they lead.
- Watch URL Shorteners: Services like TinyURL or Bitly can hide the real destination.
Scammers love creating website names that seem real but lead you somewhere unexpected - often to a dangerous place that can infect your computer.
Here’s how they do it:
Familiar Words Trick:
- They use just enough recognizable words to confuse you.
- At first glance, it seems legit. But look closer - it’s bogus.
Example:
- Imagine you get emails claiming to be from your university (like UIowa).
- The links say:
- But both are fake! Here’s why:
- The first one has “uiowa.edu,” but ends with “.ru” (Russia). Unlikely for UIowa.
- The second one lacks a proper name - it’s just an IP address. Suspicious!
Watch for Letter Swaps:
- Scammers might replace letters with numbers (like u1owa instead of uiowa).
- Or use zeros instead of the letter “o” (like its.ui0wa).
Scammers can easily fake the “from” or “reply-to” line in an email. But you can dig deeper to uncover the message’s true origin.
Here’s how it works:
Message Headers:
- When you receive an email, it has standard info like “to,” “from,” and “subject.”
- But there’s a more detailed header that reveals the email’s real source.
Suspicious Signs:
- If the “from” in the basic header doesn’t match the full header, be wary.
Example:
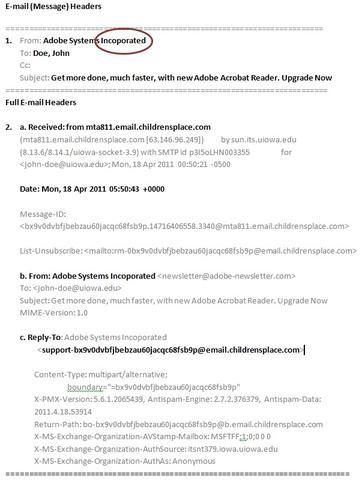
- The email header says it’s from Adobe.
- But the full header shows a host name like ‘mta811.email.childrensplace.com’.
- Childrensplace.com is a kids’ shopping site - not where Adobe emails come from!
Check the “Reply To”:
- The full header might reveal a different “reply to” address.
- In our example, it’s ‘support-bx9v0dvbfjbebzau60jacqc68fsb9p@ email.childrensplace.com’.
- Not the ‘newsletter@ adobe-newsletter.com’ it claimed to be.
Bonus Tip: Spelling Errors:
- Did you spot the misspelling of “incorporated” in the “from” line? (From: Adobe Systems Incoporated)
- Spelling mistakes are red flags for potential scams.
Stay sharp and protect yourself from sneaky emails