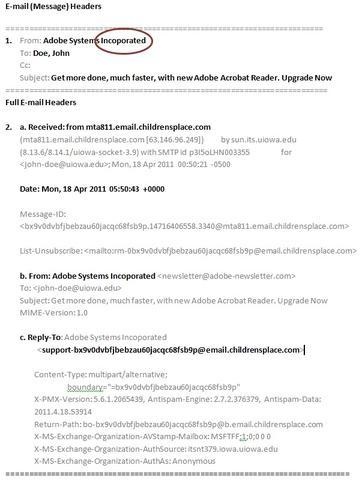
Phishing (pronounced like “fishing”) is a sneaky trick used by cyber-criminals to steal your personal information. They do this by pretending to be someone trustworthy, like a friend or a company you know.
These cyber-criminals send fake emails, create fake websites, or even send text messages (SMS) to trick you. Imagine they’re like digital fishing hooks trying to catch your sensitive information, such as credit card numbers, usernames, passwords, or Social Security numbers.
Here’s what you need to remember:
- Always be cautious when you receive messages, especially if they ask you to click on links or open attachments.
- Trust your instincts. If something feels off, it probably is!
- If you receive a suspicious message, delete it right away. Don’t click on any links or reply to it.
- To learn more about protecting yourself from phishing, watch a short video on the Microsoft Support Article titled “Protect yourself from phishing.” It explains how to spot these tricky messages.
- If you’re unsure whether a message is a phishing scam, check our current Phishing Examples and SMS Phishing (Smishing) Examples page. We post messages that others have reported.
- And if you don’t find your message there, report it to our email security team.
| IT staff or any University or hospital employee will never ask for your password or DUO code. If someone does, stop all communication immediately and contact the Help Desk. If you believe your account has been compromised, reset your HawkID password right away and notify the Help Desk. ITS Help Desk Phone: 319-384-4357 Email: its-helpdesk@uiowa.edu HCIS Help Desk Phone: 319-356-0001 Email: helpdesk-hcis@uiowa.edu |